Intelligence officers belonging to the Law Enforcement Command of the Islamic Republic of Iran, or FARAJA, are using spyware to monitor members of minority groups, including Christians, according to new research.
Since March 2020, at least 487 devices have been infected with “BouldSpy”, which has the capability to extract data including photographs, screenshots of conversations, and recordings of video calls from applications including WhatsApp and Telegram, according to researchers at US-based Lookout Threat Intelligence.
And most victims live in minority areas, such as Kurdistan, Sistan and Baluchestan, as well as West Azerbaijan Province, where many Armenian and Assyrian Christians live.
“In particular, about 25 victim locations were gathered in the city of Orumiyeh, West Azerbaijan Province, which is historically associated with Armenian and Assyrian Christianity,” Kyle Schmittle, Lookout Threat Intelligence Researcher, explained to Article18.
“Some files stolen from victims indicate Christian faith, particularly snippets or scanned sections of relevant books,” he added.

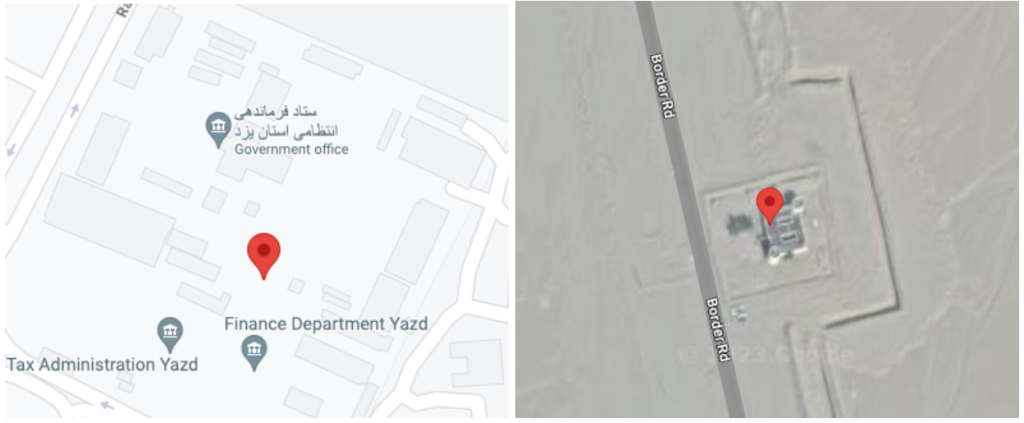
Mr Schmittle said the researchers were confident FARAJA was behind the infections, because “the first location collected from victim devices was in the direct vicinity of either a regional police station, a border control post, Iranian Cyber Police building, military facility, provincial police command headquarters, narcotics police station, or Islamic Republic of Iran Police Force Headquarters. Most of these categories of facilities fall under the ultimate command of the overarching Law Enforcement Command of the Islamic Republic of Iran, or FARAJA”.
“Because of the consistency in first-location collections from victim devices near police stations all over Iran, we believe the BouldSpy malware is most likely installed using physical access to the device when a victim is detained,” Mr Schmittle told Article18. “Additionally, some victims had photos of official FARAJA documents on their devices indicating that they had been arrested. While this information led us to attribute the malicious activity to FARAJA, in our opinion this is insufficient information to achieve a high confidence attribution.”
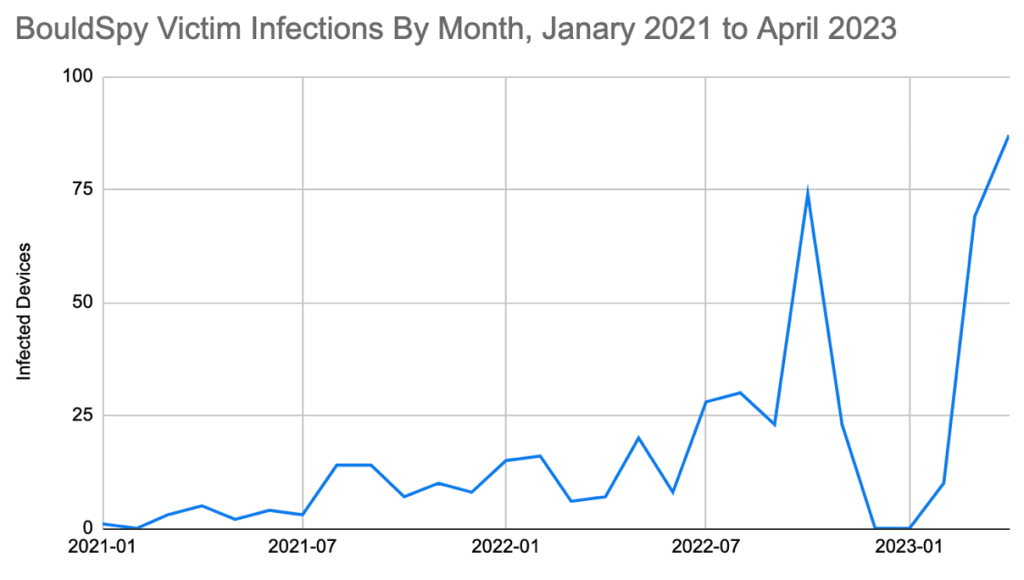
There was a particular spike in infections at the height of the Mahsa Amini protests in October 2022, Mr Schmittle noted, explaining: “We saw an infection rate of roughly 23-30 devices per month from July to September 2022, with a jump to 74 devices in October, and again back to about 23 devices in November.”
Mr Schmittle added that infections are “ongoing”, and that there has been another uptick in recent months.
“Similar numbers of devices have been infected in March and April 2023, with 69 and 87 new infections respectively, suggesting another large increase in infection activity,” he said.
The true number of victims is also likely to be higher, the researchers noted, because exfiltration data is often cleared.




0 Comments